The release of the NIST Cybersecurity Framework (CSF) 2.0 marks a significant change in the well-known and widely accepted cybersecurity framework. The framework has always provided organizations with a structured approach to managing and mitigating cybersecurity risks, serving as a crucial tool for bolstering resilience in the face of evolving cyberthreats. Equally important is the framework’s ability to offer a common language for communication between various stakeholders, enabling organizations to understand their cybersecurity posture better and prioritize investments and efforts accordingly.
While the 2.0 changes are not drastic in concept to sophisticated cybersecurity professionals, they will require all NIST CSF adopters to update their frameworks in various ways to meet the 2.0 requirements. Below, FORVIS summarizes the key changes to NIST CSF 2.0.
6th Function
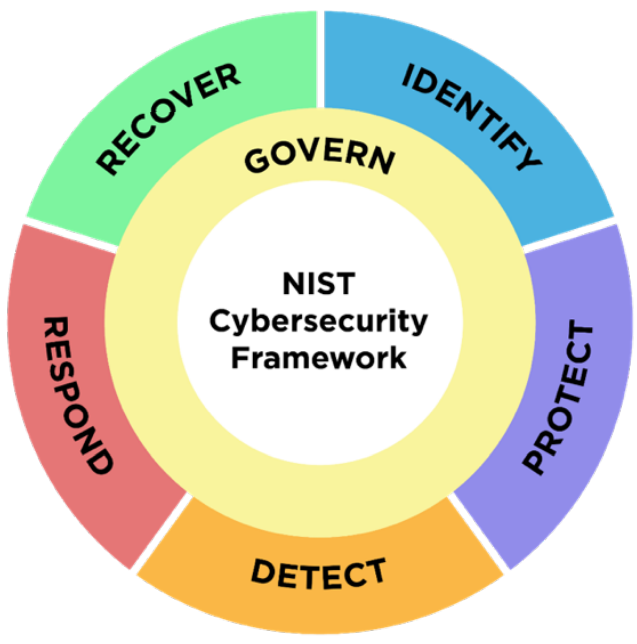
NIST CSF 2.0 added a sixth function called “Govern” to the pre-existing functions: Identify, Protect, Detect, Respond, and Recover. The addition of the Govern function underscores the importance of cybersecurity governance within organizations. This function emphasizes the need for clear policies, procedures, and oversight mechanisms to ensure effective cybersecurity management at all levels. This addition reflects the recognition that effective governance is essential for achieving and sustaining cybersecurity resilience in today’s rapidly changing digital landscape.
- NIST Cybersecurity Framework
- Govern
- Identify
- Protect
- Detect
- Respond
- Recover
- Govern
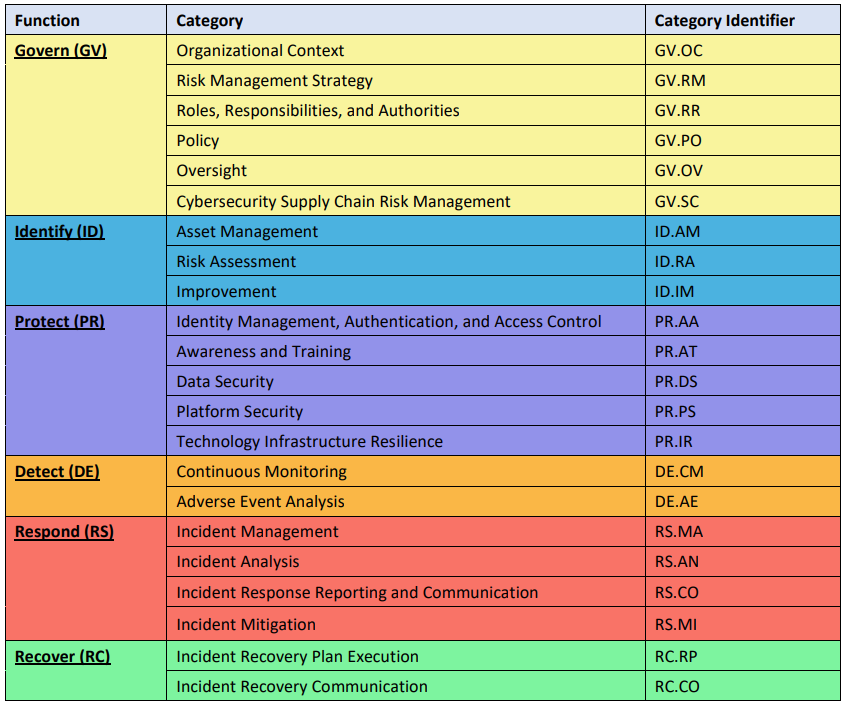
- Function
- Category
- Category Identifier
- Category
- Govern (GV)
- Organizational Context
- GV.OC
- Risk Management Strategy
- GV.RM
- Roles, Responsibilities, and Authorities
- GV.RR
- Policy
- GV.PO
- Oversight
- GV.OV
- Cybersecurity Supply Chain Risk Management
- GV.SC
- Organizational Context
- Identify (ID)
- Asset Management
- ID.AM
- Risk Assessment
- ID.RA
- Improvement
- ID.IM
- Asset Management
- Protect (PR)
- Identity Management, Authentication, and Access Control
- PR.AA
- Awareness and Training
- PR.AT
- Data Security
- PR.DS
- Platform Security
- PR.PS
- Technology Infrastructure Resilience
- PR.IR
- Identity Management, Authentication, and Access Control
- Detect (DE)
- Continuous Monitoring
- DE.CM
- Adverse Event Analysis
- DE.AE
- Continuous Monitoring
- Respond (RS)
- Incident Management
- RS.MA
- Incident Analysis
- RS.AN
- Incident Response Reporting and Communication
- Incident Mitigation
- RS.MI
- Incident Management
- Recover (RC)
- Incident Recovery Plan Execution
- RC.RP
- Incident Recovery Communication
- Incident Recovery Plan Execution
Edited Categories & Subcategories
There are a number of changes made to predecessor CSF 1.1 Categories and Subcategories, which include renaming, moving, and eliminating. The CSF 2.0 changes are intended to reorganize the controls and introduce new content in ways that are relevant to securing our critical infrastructure. The Informative Reference provides a mapping between not only CSF 2.0 and CSF 1.1, but also with other frameworks.
Implementation Examples
Throughout the NIST CSF 2.0 materials there are references to implementation examples, which are exactly as they sound—short descriptions of how each subcategory control could be implemented at an organization. Most subcategories include multiple examples, so this is very useful to contextualize the intent of the control and how you might see it in action.
| Function | DETECT (DE): Possible cybersecurity attacks and compromises are found and analyzed |
|---|---|
| Category | Adverse Event Analysis (DE.AE): Anomalies, indicators of compromise, and other potentially adverse events are analyzed to characterize the events and detect cybersecurity incidents |
| Subcategory | DE.AE-02: Potentially adverse events are analyzed to better understand associated activities |
| Implementation Example | Ex1: Use security information and event management (SIEM) or other tools to continuously monitor log events for known malicious and suspicious activity Ex2: Utilize up-to-date cyberthreat intelligence in log analysis tools to improve detection accuracy and characterize threat actors, their methods, and indicators of compromise |
Increased Focus on Integrating With Other Risk Management Programs
Organizations will have varying approaches to managing additional risks beyond cybersecurity or happen to overlap with cybersecurity, e.g., supply chain risk, privacy risk, and artificial intelligence. The CSF 2.0 framework outlines this and provides support for the integration of risk management to complement and enhance the overall cybersecurity posture. (Example: NIST 800-37 Risk Management Framework for Information Systems and Organizations)
Additional examples include:
- Supply Chain Risks – One of the most distinguishable differences in CSF 2.0 compared to its predecessor lies in its increased focus on supply chain security and resilience. With the growing interconnectedness of businesses and reliance on third-party vendors, the new framework emphasizes the importance of assessing and managing risks throughout the supply chain. It also appropriately recognizes that broader supply chain risks need to be addressed and NIST has developed additional frameworks to address this risk. (Example Integrated Framework: NIST 800-161 Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations)
- Privacy Risks – The intersection of cybersecurity and privacy is important to understand and recognize as well. While confidentiality, integrity, and availability are overlapping tenets, privacy risks are broader than cybersecurity; therefore, an integrated approach to managing cybersecurity and other risks is essential to a strong privacy program. (Example Integrated Framework: NIST Privacy Framework)
- Risks From Emerging Technologies – CSF 2.0 intends to integrate with the risk management of emerging technologies and trends, such as cloud computing, IoT devices, and AI-driven systems. By acknowledging these advancements and how they are managed within broader enterprise risk management programs, the framework strengthens its adaptability and resilience in the face of evolving threats and technological developments. (Example Integrated Framework: NIST Artificial Intelligence Risk Management Framework)
Overall, the release of CSF 2.0 underscores the ongoing commitment to enhancing cybersecurity practices and provides organizations with a comprehensive framework to navigate the complex cybersecurity landscape effectively.
As your organization dives deeper into the CSF 2.0 framework and updates, do not hesitate to reach out to FORVIS for guidance and suggested approaches to convert from CSF 1.1 to CSF 2.0.

